Application of artificial intelligence in security field
Artificial Intelligence (abbreviated as AI) began in the middle of the 1950s, and then developed in decades. At the end of the 1980s, with the rise of artificial neural network research, artificial intelligence entered a new stage. In particular, in recent years, deep learning has achieved breakthroughs in the optimization of artificial neural networks, making it possible for machine aids and expanding the field of application of artificial intelligence.

First of all, there are a few things to be aware of: AI is a rigorous science, focused on designing intelligent systems and smart machines, and the algorithmic techniques used in it are to some extent borrowed from our understanding of the brain. Many modern AI systems use artificial neural networks and computer code to simulate a very simple network of interconnected units, somewhat like the neurons in the brain. These networks can learn experience by changing the connections between cells, a bit like the brains of humans and animals learn by modifying the connections between neurons. Modern neural networks can learn to recognize patterns, translate languages, learn simple logical reasoning, and even create images and create new ideas. Among them, pattern recognition is a particularly important function - AI is very good at identifying patterns in large amounts of data, which is not so easy for humans.
A particularly useful architecture in deep learning systems is called Convolutional Neural Networks or ConvNet. ConvNet is a specific way of connecting elements in a neural network and is inspired by other animal and human visual cortical architectures. Modern ConNet can use from 7 to 100 layers of units. In the park, we humans see Collie and Chihuahua. Although they are different in body size and weight, we know that they are dogs. For computers, the image is just an array of arrays. Within this array of arrays, local patterns, such as the edges of objects, can be easily detected in the first layer. The next layer of the neural network will detect simple combinations of these simple patterns, such as the wheels of a car or the eyes of a human face. The next layer will detect certain parts of the objects that are formed by these combinations of shapes, such as faces, legs, or airplane wings. The last layer of the neural network will detect the combination of those parts: a car, an airplane, a person, a dog, and so on. The depth of the neural network - how many layers it has - enables the network to recognize complex patterns in this hierarchical manner.
Once trained in a large number of sample databases, ConvNet is particularly useful for identifying natural signals such as images, videos, voice, music, and even text. In order to train the network well, we need to provide a large amount of image data that these networks are tagged. ConvNet will learn to correlate each image with its corresponding label. Interestingly, ConvNet can also pair images that have never been seen before and their corresponding tags. So we got a system that can sort all sorts of images and identify the elements in the photos.
In the field of security, with the constant advancement of the construction of the safe city, there are more and more monitoring points. From the first few thousand roads to tens of thousands of roads, and even to the scale of hundreds of thousands of roads, there are massive amounts of video and bayonet production. The data. At the same time, with the development of related technologies such as high-definition video, intelligent analysis, cloud computing, and big data, security is progressing from traditional passive defense to active judgment and early warning, and the industry has also applied and promoted multiple industries from a single security field. The direction of production efficiency and the improvement of the intellectualization of life is to provide visual and intelligent solutions for more industries and people. With the development of security, the important role of artificial intelligence is gradually emerging. Currently, users are faced with massive amounts of video data, which cannot be easily retrieved and analyzed using human-sea tactics. Artificial intelligence is required as an expert or assistant to analyze video content in real time, detect abnormal information, and perform risk prediction.
First, artificial intelligence technology
In recent years, Suzhou Qianxuntong has been developing intelligent technology. After years of accumulation, its intelligent technology has been used in all aspects of the product line. As the goal of intelligent technology development, “artificial intelligenceâ€, we are even more determined than ever. The pursuit. Based on the present, looking ahead, we focus our current artificial intelligence research and development on video structuring technology and big data technology.
1 . Video structuring technology
Video structuring technology is the most advanced artificial intelligence technology that integrates machine vision, image processing, pattern recognition, deep learning, and is the cornerstone of video content understanding.
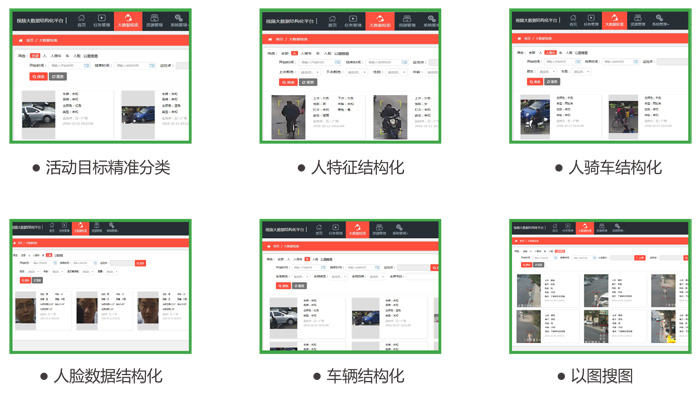
Video structuring can be divided into three steps in the technical field: target detection, target tracking, and target attribute extraction.
The target detection process is to extract the foreground target from the video, and then identify whether the foreground target is a valid target (such as: people, vehicles, faces, etc.) or an invalid target (such as leaves, shadows, light, etc.). The target detection process is mainly applied to technologies such as moving target detection, face detection, and vehicle detection.
The target tracking process is to achieve continuous tracking of a specific target in the scene, and acquire a high-quality picture as a captured picture of the target from the entire tracking process. In the target tracking process, it mainly applies to multi-target tracking, target fusion, and target scoring technology.
The target attribute extraction process is the identification of the target attributes in the target picture that has been detected, and it is judged which target has the visual characteristic attributes such as the gender, age, dress of the target, the vehicle model, color and other attributes of the target. The target attribute extraction process is mainly based on feature extraction and classification technology of deep learning network structure.
At the same time, in order to solve the problem of high-performance analysis and calculation of video structuring, we launched the “Thousands of Views†video structuring server in 2016, making full use of the parallel processing capabilities of multi-GPUs to improve the comprehensive performance of video structuring processing.
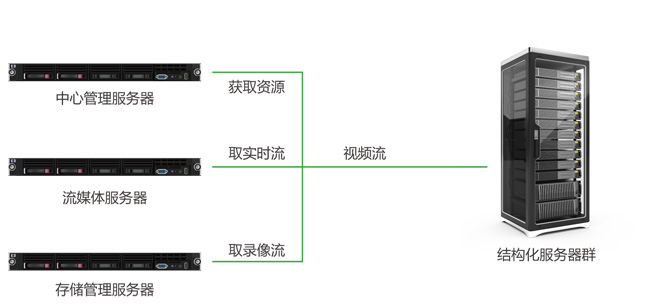
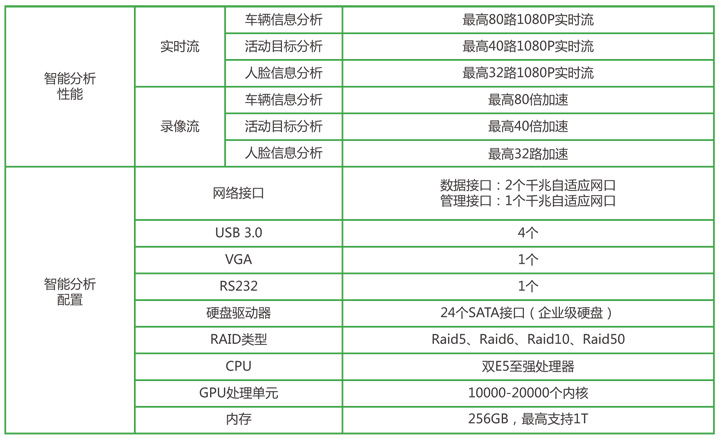
2 . Big data technology
Big data technology provides powerful distributed computing capabilities and knowledge base management capabilities for artificial intelligence. It is an important support for artificial intelligence analysis and prediction and self-improvement. It consists of three parts: massive data management, large-scale distributed computing, and data mining.
Mass data management is used to collect and store the full range of data resources involved in artificial intelligence applications, and to accumulate data based on the time axis so that the rules of real things can be reflected in the time dimension. At the same time, the huge knowledge base that artificial intelligence applications have accumulated for a long time also needs to rely on the system for management and access.
Large-scale distributed computing makes artificial intelligence powerful computing capabilities, can analyze a large amount of data at the same time, carry out feature matching and model simulation, and provide personalized services for many users.
Data mining is the core of the real value of artificial intelligence. It uses machine learning algorithms to automatically carry out multiple analysis and calculations, explores the laws and abnormal points in data resources, and assists users to find effective resources more quickly and accurately, and carries out risk prediction and assessment. .
Second, artificial intelligence applications
The rapid development of the current artificial intelligence technology has actively promoted the security field toward a more intelligent and humanized direction, mainly reflected in the following aspects:
1 . Application in * industry
* The urgent need of industry users is to find clues to criminal suspects in massive video information. Artificial intelligence has natural advantages in feature extraction and content understanding of video content. An intelligent video analysis system can analyze video content in real time and afterwards, detect moving objects, identify people and car property information, and deliver it to the back-end artificial intelligence central database through the network for storage. Massive city-level information is aggregated, and with the use of powerful computational capabilities and intelligent analysis capabilities, artificial intelligence can analyze the suspect’s information in real time, give the most probable clues, and lock the trajectory of suspects for a few days. , shortened to a few minutes, saving precious time for the detection of the case. Its powerful interactive ability can also communicate with the case police in natural language, and it truly becomes the expert assistant of the case-handling staff.
Taking the vehicle characteristics as an example, vehicle tracking can be performed by using a small electric fan in front of the driving position of the vehicle to lock the trajectory of the suspected vehicle involved in the massive video resources.
2 . Application in the transportation industry
In the field of transportation, with the large-scale networking of traffic bayonet, collecting information on the traffic records of massive vehicles plays an important role in urban traffic management. By using artificial intelligence technology, urban traffic flow can be analyzed in real time, traffic light intervals can be adjusted, and vehicle waiting time can be shortened. Time, improve the efficiency of urban roads. The city-level artificial intelligence brain can control the trajectory information of the vehicles on the road in real time, the vehicle information in the parking lot, and the parking information in the residential area. It can predict traffic flow changes and changes in the number of parking spaces in advance half an hour, and rationally allocate resources. To divert traffic, realize large-scale traffic linkage scheduling at airports, railway stations, bus stations, and commercial districts, improve the operating efficiency of the entire city, and provide guarantees for residents' unimpeded travel.
3 . Application in smart buildings
In the field of intelligent buildings, artificial intelligence is the brain of buildings, which comprehensively controls the security and energy consumption of buildings, real-time tracking and positioning of people, vehicles, and objects entering and leaving buildings, distinguishing between office workers and outsiders, and monitoring the energy consumption of buildings. Makes the building's operating efficiency optimal, extending the life of the building. Intelligent artificial intelligence core of the building collects the monitoring information and credit card records of the entire building. The indoor camera can clearly capture the information of the personnel. When the card is used for access control, the information of the pass card and the face information of the card reader are compared in real time, and the card swiping behavior is detected. It can also distinguish the trajectory and stay of staff in the building, and find violations of visits to ensure the safety of the core area.
4 . Application in factory park
Industrial robots have been around for a long time, but most of them are operational robots that are fixed on the production line. Mobile patrol robots will have a wide range of applications in fully enclosed unmanned factories. In the factory park site, security cameras are mainly deployed at entrances and exits and perimeters. The location of the interior corners cannot be covered. These places are just the corners of security risks. The mobile patrol robots are used to patrol regularly to read instruments. Values, analysis of potential risks, guarantee the reliable operation of fully enclosed unmanned factories, and truly promote the development of “Industry 4.0â€.
5 . Application in civil security
In the field of civil security, each user is highly individualized. It uses the powerful computing power and service capabilities of artificial intelligence to provide differentiated services for each user, enhances the sense of security of individual users, and truly meets the growing needs of people. service requirements. Taking home security as an example, when no person is detected in the home, the home security camera can automatically enter the deployment mode. When there is an abnormality, the intruder is given a voice warning and remotely informed the home owner. When family members return home, they can automatically disarm and protect user privacy. During the night, through self-study for a certain period of time, the family members will be kept abreast of the laws of rest. When the owner breaks the rest, the arming is activated to ensure night security, eliminating the need for artificial arming and realizing humanity.
Third, there are problems
The application of artificial intelligence in the field of security has a very good prospect, but at present the domestic foundation is still relatively weak, there are still many problems in the application process that need to be improved and solved:
1) The quality of video imaging is greatly affected by the environment, there are problems such as insufficient illumination, blurred images, too small target size or mutual obstruction, which is not conducive to the identification of video content by artificial intelligence.
2) The data resources are scattered, the degree of openness and sharing is low, and it is difficult to carry out multifaceted data fusion analysis, which makes artificial intelligence lack effective data support.
3) Insufficient accumulation of domain expertise. The early intelligence analysis technology belongs to the single scene target detection and behavior analysis. The ability to understand video content is weak. At the same time, it does not involve the analysis of the associated behavior of large-scale scenes. It does not accumulate effective experience knowledge for abnormal analysis and risk. prediction.
4) Lack of effective self-improvement capabilities. At present, a lot of intelligence is just a kind of reactive intelligence, which automatically judges according to input conditions and does not have the ability to grow. Artificial intelligence should have accumulated experience based on time, as well as the ability to share experience among groups, in order to continue to improve, making smart capabilities more powerful and more efficient.
Summary <br>
Artificial intelligence is the future of security. There are many obstacles and difficulties that need to be overcome and overcome on the road to the future. However, the overall trend is optimistic. We firmly believe that only people who are autonomous, personalized, and constantly evolving The intelligent brain can solve the ever-increasing demand in the field of security and become experts and assistants of vast numbers of users. It will raise the level of intelligence in the entire security field and promote the upgrading of the security industry.
Shandong Heli Machinery Co.,Ltd , https://www.chinaheliblower.com
